You’ve probably read a lot about hackers and how to protect your computer, but for some reason, most people don’t really care all that much about smartphone security.
Maybe because it’s not like a traditional hard drive where you store all your documents, images, videos, etc, but today’s hyperactive smartphone users store a lot of information that is quite sensitive and that others, like hackers, would gladly enjoy taking while you’re surfing the web at Starbucks.
Luckily, smartphone security is gaining traction and there are quite a few things you can do to help prevent your smartphone from being hacked. Actually, a lot of same measures you take to protect your computer can be used to protect your smartphone too. If you have any of your own tips for securing your smartphone, let us know in the comments.
1. Use Passcodes Everywhere
Whether you have an Android phone or an iPhone, you can prevent access to your device by adding a passcode or a lock pattern on Android. This simple security measure can prevent sensitive information from being viewed by others.
This is especially important if you have a bunch of apps installed where personal data is stored like financial apps (Mint, bank apps, etc), journal apps (DayOne), note apps (Evernote), etc. On some of these apps like Mint and DayOne, you can add a passcode specifically for that app, which I always do in addition to the passcode to protect the home screen.
The home screen passcode is important because a lot of the email apps (Mail on iPhone and Gmail on Android) don’t even have an option to passcode your email. Emails can contain a lot of private information and since most people go to parties and leave their phones on tables and counters, it’s very easy for someone to snoop around your stuff.
2. Protect Your iCloud & Google Account
The second thing most people don’t realize is that if someone can get into your iCloud or Google account, they can gain access to a lot of data that you might be creating and editing from your smartphone. In these times, it’s a necessary inconvenience to enable 2-step verification on both of these accounts. I’ve written about how to secure your Google account and how to properly setup backup and recovery options for 2-step verification.
It’s pretty ridiculous, but your Apple ID basically controls access to every single Apple service that currently exists from iTunes to iCloud to FaceTime to iMessage, etc, etc. If someone can access your Apple ID, they can wreak havoc on your Apple life including erasing your iPhone, iPad and Mac remotely.
It’s pretty much the same issue with Google. Your Google account basically logs you into all Google services from YouTube to Gmail to Google Play to Google Maps to Google Calendar to Picasa to Google+, etc, etc, etc.
3. Avoid Jailbreaking or Rooting Your Smartphone
If you really know what you’re doing and you jailbreak or root your phone for fun and enjoyment, then good for you. If you want to do it because you heard about it in the news and want to be “free” from constraints and restrictions, then you should avoid the process altogether.
Firstly, it can mess up your phone and cause you more grief than happiness. Secondly, you won’t be able to update your phone with the latest updates to the OS since it’ll be in an unsupported mode.
Yes, you can install some apps and customize settings that you could otherwise not do, but that means you’re also downloading apps that may contain malicious software. You already have that problem on Android since they are not as restrictive as Apple about what goes into the app store. Which brings us to the next point.
4. Be Careful With the Apps You Install
This is especially important on Android devices. Google recently removed 50,000 apps that were suspected of being malware. There won’t be any shortage of apps that contain malware, viruses or other sneaky software to steal your data or damage your phone.
The Apple app store also has this problem, but to a much lesser extent. Apple vets each app before it gets listed in the store and routinely goes about removing apps from the store that are deemed to be violating store policies.
Check out this article that talks about how more than 32 million Android devices were infected with malware in 2012 and how 95% of malware is targeted towards Android devices.
It’s fine if you hate Apple, but the fact is that if you own an Android device, you have to be very careful about downloading apps. Check the reviews, check to see if they have a website, do a search in Google with the app name, etc.
5. Use an App Instead of the Browser
If you’re doing banking on your phone or stock trading or anything else that passes sensitive information between your phone and the Internet, it’s best to use an official app for that site or company rather than opening using the browser on your phone.
For example, Chase, Bank of America, Vanguard, ScottTrade, Mint, and lots of other big financial institutions have their own apps for iOS and Android. Secure connections are supported on smartphone browsers also, but you’ll be a little bit safer if you get an official app that may have extra security features.
6. Control What an App Can Access
You’ve probably seen the following message on your iPhone a hundred times already:
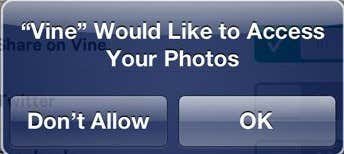
There are all sorts of these “AppName Would Like to Access Your Data” messages. Data can be photos, location, contacts, etc, etc. Always be mindful and don’t just click OK all the time. If you click anything all the time, it’s better to just choose Don’t Allow and if you really can’t use the app later on, you can manually go back in and change it to allow access. Most of these are very legitimate requests and won’t cause any harm, but it’s better to be safe.
On Android, it’s again worse because some apps will ask for permissions to everything even though they don’t need it. You can read this Lifehacker post on how to protect yourself from Android apps that request too many permissions. There are also a lot more permissions on Android than there are on iOS, so again you have to be more careful if you’re an Android user.
7. Keep Data Backed Up
It’s not only a good idea to keep your smartphone backed up in case you drop it in the toilet, but also if it gets stolen and you have to remotely wipe it clean. Apple users can install the Find My iPhone app, which will let you remotely lock a phone and remotely wipe it if you know it’s been stolen.
If you don’t have your data backed up, you’ll lose it all if it’s stolen. If you back it up locally or in the cloud, you’ll be able to wipe your phone and get all your data back on your new phone. You can either sync your smartphone to your computer using iTunes or you can back it up to the cloud via iCloud.
On Android, there is a built-in backup tool, but it doesn’t backup everything on your phone like the iOS does. Instead, you’ll have to rely on third-party apps in the Google Play store to backup your phone completely. Note that Android also has a remote wipe feature, but you need to setup it first by installing certain apps.
8. Report Your Phone Stolen
In the last few months, there has been a stolen phone database created that is shared between the major wireless carriers. You can report your phone stolen and that will prevent anyone from connecting to the carrier and using data or minutes.
If they try to wipe it, replace the SIM, etc, it still won’t allow them to activate on any of the carriers because of the serial number. You can visit the following pages to report your smartphone stolen and prevent the thief from connecting to any wireless carrier:
AT&T, Verizon, Sprint, T-Mobile
9. Update the OS
Just like you have to constantly install Microsoft security updates for your PC, it’s a good idea to install the latest updates for your smartphone. You can wait a few days and make sure there are no major issues with the update like degradation of battery life, etc, but if nothing stands out, then update the phone.
In addition to updating the OS, it’s also a good idea to update the apps installed on your phone. It’s amazing how many smartphones I’ve come across where there are 10, 20, 30+ apps that have updates of which none have been installed. Those updates may include new features, but a lot of them are bug fixes, performance updates and security fixes.
10. Wireless & Bluetooth
When you’re not at home, it’s best to try to disable the wireless and bluetooth altogether and use your 3G or 4G connection if you can. The moment you connect to an untrusted wireless network, you’re open to hackers scanning for victims over the network. Even if you’re not banking or doing something else that involves sensitive data, a hacker can still try to connect to your smartphone and steal data, etc.
When it comes to Bluetooth, hacking is less common, but it’s gaining popularity as people start to use the technology more beyond just headsets. Now you have watches connected to your phone via bluetooth and fitness bands and a whole host of other gadgets. If bluetooth is enabled and discoverable, it gives hackers another way to possibly see the data being passed between the bluetooth device and your phone.
Hopefully these tips will help you in the unfortunate case where you phone is lost or stolen. I’ve personally had to wipe an iPhone because I lost it and later realized someone was using the apps and data connection. That definitely won’t happen again, even if my phone is lost or stolen because I’ve made sure it’s as protected as possible. If you have any other tips for securing your smartphone, let us know in the comments. Enjoy!