Do you just select Accept to everything thrown at you when you install a new app on your Android device? Most people do. But what are you agreeing to?
There’s the End User Licensing Agreement (EULA) and then there are the app permissions. Some of those app permissions can allow an app, and the company that made it, to go too far and violate your privacy. You need to know what app permissions to avoid agreeing to on your Android.

What permissions should you avoid? It depends, and we’ll go into that further. You’ll want to be wary of permissions related to accessing:
- Phone
- Audio
- Location
- Contacts
- Camera
- Calendar
- Messaging
- Biometrics
- Cloud Storage
What Are App Permissions?
When you install an app, the app seldom comes with everything it needs to do its job already built-in. There are a lot of things already in your Android that the app needs to integrate with to get its job done.

Let’s say you download a photo editing app. The app developer wouldn’t write in a complete photo gallery or camera software into the app itself. They’re just going to ask for access to those things. This keeps the apps small and efficient and your Android from filling up with duplicated app code.
What App Permissions Should I Avoid?
For Android developers, permissions are divided into 2 groups: normal and dangerous.
Normal permissions are considered safe and often allowed by default without your express permission. Dangerous permissions are ones that may present a risk to your privacy.
We’ll look at the 30 dangerous permissions listed in the Android Developer’s Reference from Google. The name of the permission will be listed, with a quote from the Developer’s Reference about what the permission allows. Then we’ll briefly explain why it could be dangerous. These are app permissions you may want to avoid, if possible
ACCEPT_HANDOVER
“Allows a calling app to continue a call which was started in another app.”
This permission allows for a call to be transferred to an app or service you might not be aware of. This could end up costing you if it transfers you to a service that’s using your data quota instead of your cell plan. It could also be used to secretly record conversations.
ACCESS_BACKGROUND_LOCATION
“Allows an app to access location in the background. If you’re requesting this permission, you must also request either ACCESS_COARSE_LOCATION or ACCESS_FINE_LOCATION. Requesting this permission by itself doesn’t give you location access.”
Like Google says, this permission alone won’t track you. But what it can do is allow you to be tracked even if you think you’ve closed the app and it’s no longer tracking your location.
ACCESS_COARSE_LOCATION
“Allows an app to access approximate location.”
The accuracy of coarse location locates you to a general area, based upon the cell tower to which the device is connecting. It’s helpful for emergency services to locate you during trouble, but no one else really needs that information.
ACCESS_FINE_LOCATION
“Allows an app to access precise location.”
When they say precise, they mean it. The fine location permission will use GPS and WiFi data to pinpoint where you are. The accuracy could be within a few feet, possibly locating which room you’re in within your home.
ACCESS_MEDIA_LOCATION
“Allows an application to access any geographic locations persisted in the user’s shared collection.”
Unless you’ve turned off geotagging on your pictures and videos, this app can go through all of them and build an accurate profile of where you’ve been based on data in your photo files.
ACTIVITY_RECOGNITION
“Allows an application to recognize physical activity.”
On its own, it might not seem like much. It’s often used by activity trackers like FitBit. But put it together with other location information and they can figure out what you’re doing and where you’re doing it.
ADD_VOICEMAIL
“Allows an application to add voicemails into the system.”
This could be used for phishing purposes. Imagine adding a voicemail from your bank asking to give them a call, but the number provided isn’t the bank’s.
ANSWER_PHONE_CALLS
“Allows the app to answer an incoming phone call.”
You can see how this could be a problem. Imagine an app just answering your phone calls and doing whatever it likes with them.
BODY_SENSORS
“Allows an application to access data from sensors that the user uses to measure what is happening inside their body, such as heart rate.”
This is another one where the information on its own might not mean much, but when coupled with information from other sensors could prove very revealing.
CALL_PHONE
“Allows an application to initiate a phone call without going through the Dialer user interface for the user to confirm the call.”
It’s scary enough to think an app could make a phone call without you knowing it. Then think about how it might call a 1-900 number and you could be on the hook for hundreds or thousands of dollars.
CAMERA
“Required to be able to access the camera device.”
A lot of apps will want to use the camera. It makes sense for things like photo editing or social media. But if a simple kids game wants this permission, that’s just creepy.
READ_CALENDAR
“Allows an application to read the user’s calendar data.”
The app would know where you’ll be and when. If you make notes with your appointments, it’ll also know why you’re there. Add to the location information and the app will know how you got there too.
WRITE_CALENDAR
“Allows an application to write the user’s calendar data.”
A bad actor might use this to put appointments in your calendar making you think you might have to go somewhere you don’t, or call someone you don’t need to.
READ_CALL_LOG
“Allows an application to read the user’s call log.”
Who we talk to and when can be very revealing about our lives. Calling your co-worker during the day? Normal. Calling them at 2 a.m. on Saturday night? Not so normal.
WRITE_CALL_LOG
“Allows an application to write (but not read) the user’s call log data.”
It’s not likely to happen, but a malicious app could add call logs to set you up for something.
READ_CONTACTS
“Allows an application to read the user’s contacts data.”
Similar to reading the call log, a person’s contact list says a lot about them. Plus, the list may be used to phish your friends, making them think it’s you messaging them. It can also be used to grow a marketing email list the company could then sell off to advertisers.
WRITE_CONTACTS
“Allows an application to write the user’s contacts data.”
What if this could be used to edit or overwrite your contacts? Imagine if it changed the number for your mortgage broker to another number and you call some scammer and give them your financial information.
READ_EXTERNAL_STORAGE
“Allows an application to read from external storage.”
Any data storage that plugs into your device, like a microSD card or even a laptop, could be accessed if you allow this permission.
WRITE_EXTERNAL_STORAGE
“Allows an application to write to external storage.”
If you grant this permission, then the READ_EXTERNAL_STORAGE permission is implicitly granted as well. Now the app can do what it wants with any connected data storage.
READ_PHONE_NUMBERS
“Allows read access to the device’s phone number(s). “
If an app asks for this and you grant it, the app now knows your phone number. Expect to get some robocalls soon if the app is sketchy.
READ_PHONE_STATE
“Allows read only access to phone state, including the current cellular network information, the status of any ongoing calls, and a list of any phone accounts registered on the device.”
This permission could be used to facilitate eavesdropping and tracking you by which network you’re on.
READ_SMS
“Allows an application to read SMS messages.”
Again, another way to eavesdrop on you and gather personal information. This time by reading your text messages.
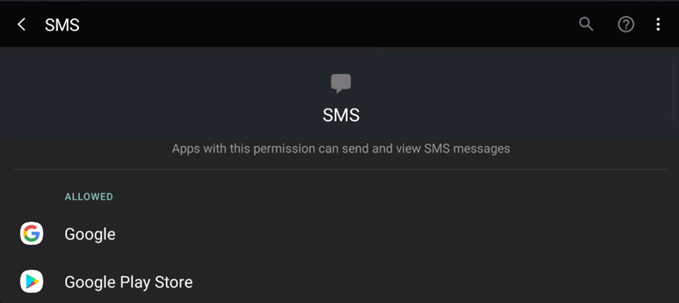
SEND_SMS
“Allows an application to send SMS messages.”
This could be used to sign you up for paid texting services, like getting your daily horoscope. This could cost you a lot of money, quickly.
RECEIVE_MMS
“Allows an application to monitor incoming MMS messages.”
The app would be able to see any pictures or videos that were sent to you.
RECEIVE_SMS
“Allows an application to receive SMS messages.”
This app would allow for monitoring your text messages.
RECEIVE_WAP_PUSH
“Allows an application to receive WAP push messages.”
A WAP push message is a message that is also a web link. Selecting the message could open a phishing or malware laden web site.
RECORD_AUDIO
“Allows an application to record audio.”
Yet another way to eavesdrop on people. Plus there’s a surprising amount you can learn from the sounds around a person, even if they’re not talking.
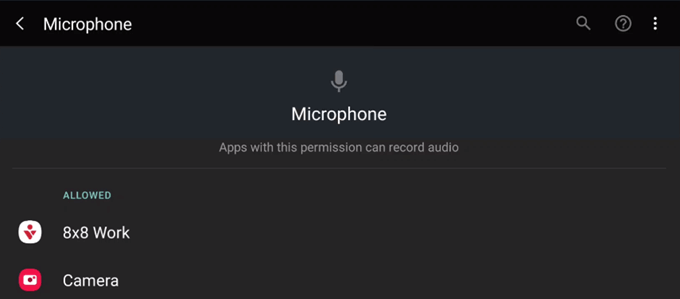
USE_SIP
“Allows an application to use SIP service.”
If you don’t know what a SIP session is, think of Skype or Zoom. Those are communications that happen over a VoIP connection. This is just one more way that a malicious app could watch and listen to you.
Should I Avoid All Android Permissions?
We must look at permissions in the context of what we want the app to do for us. If we were to block all those permissions for every app, none of our apps would work.
Think of your Android device as your home. For our analogy, think of the app as a repairman coming into your home. They have a specific job to do and will need access to certain parts of your home, but not others.
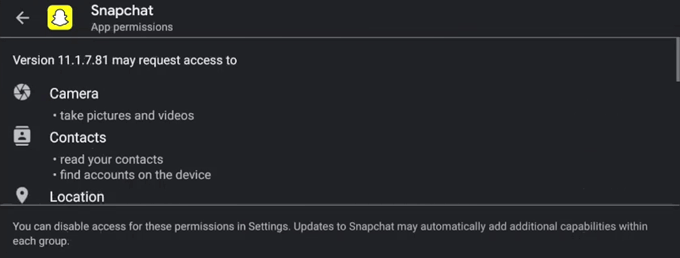
If you’ve got a plumber coming in to fix the kitchen sink, they’re going to need your permission to access the sink and the pipes that supply and remove water. That’s it. So if the plumber asked to see your bedroom, you’d become suspicious of what they’re doing. The same goes for apps. Keep that in mind when you agree to app permissions.